Journal
In the blog we write news about the life of our project, development of new devices, useful articles and tips about privacy and safe use of gadgets.

Digital Forensics: Investigating Crimes Through...
Digital Forensics: Investigating Crimes Through Digital Traces and Protecting Electronic Evidence Mobile devices have fundamentally transformed crime investigation methods. In the past, investigations mainly relied on fingerprints and physical evidence....
Digital Forensics: Investigating Crimes Through Digital Traces and Protecting Electronic Evidence
Digital Forensics: Investigating Crimes Through Digital Traces and Protecting Electronic Evidence Mobile devices have fundamentally transformed crime investigation methods. In the past, investigations mainly relied on fingerprints and physical evidence....

The School Phone Ban: Proper Implementation of ...
The use of smartphones in schools has been a topic of heated debate worldwide. Countries like France, China, and Sweden have already implemented strict regulations, banning mobile phones during lessons...
The School Phone Ban: Proper Implementation of a Necessary Measure
The use of smartphones in schools has been a topic of heated debate worldwide. Countries like France, China, and Sweden have already implemented strict regulations, banning mobile phones during lessons...

Velter signs an agreement with Cyberkov and ent...
At the GITEX 2024 exhibition in Dubai, Velter, a Russian developer of digital privacy solutions, signed an agreement with Cyberkov, a leader in cybersecurity in the Middle East. As...
Velter signs an agreement with Cyberkov and enters the Middle Eastern market
At the GITEX 2024 exhibition in Dubai, Velter, a Russian developer of digital privacy solutions, signed an agreement with Cyberkov, a leader in cybersecurity in the Middle East. As...

Leak Confirms: Advertisers Are Listening In – T...
In a world increasingly reliant on technology, concerns about privacy have reached new heights. Many users have long suspected their phones and smart devices were "listening in" on their...
Leak Confirms: Advertisers Are Listening In – The Reality of "Ad Eavesdropping"
In a world increasingly reliant on technology, concerns about privacy have reached new heights. Many users have long suspected their phones and smart devices were "listening in" on their...
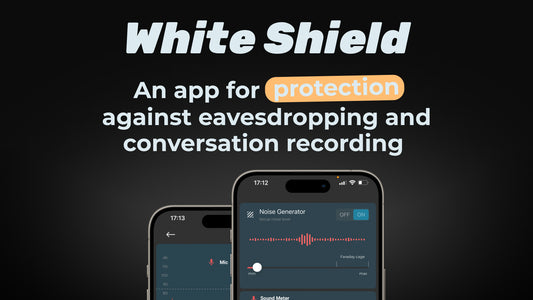
White Shield: An App for Protecting Conversatio...
A device with an always-active microphone inherently poses a privacy threat, and what could be a more fitting example than a smartphone—always listening, always online? To protect your privacy...
White Shield: An App for Protecting Conversations from Eavesdropping and Recording
A device with an always-active microphone inherently poses a privacy threat, and what could be a more fitting example than a smartphone—always listening, always online? To protect your privacy...

Fashion Tech Solutions for Modern Digital Privacy
Fashion Tech represents the seamless integration of fashion and technology, and Velter is at the forefront of this evolution. In an era where digital privacy is becoming increasingly critical,...
Fashion Tech Solutions for Modern Digital Privacy
Fashion Tech represents the seamless integration of fashion and technology, and Velter is at the forefront of this evolution. In an era where digital privacy is becoming increasingly critical,...

Unplug and Protect: Why You Need a Faraday Dry Bag
The Faraday Dry Bag is a cutting-edge waterproof and radio-blocking bag designed to safeguard digital privacy and secure electronic devices. Constructed with a 400D waterproof nylon exterior and a...
Unplug and Protect: Why You Need a Faraday Dry Bag
The Faraday Dry Bag is a cutting-edge waterproof and radio-blocking bag designed to safeguard digital privacy and secure electronic devices. Constructed with a 400D waterproof nylon exterior and a...

The Future of Airplane Mode: Smart Devices Deci...
Google has patented a new "Connected Flight Mode" technology, promising an evolution in airplane mode functionality. Unlike the current manual mode, this smart airplane mode will autonomously determine which...
The Future of Airplane Mode: Smart Devices Decide What to Enable and Disable
Google has patented a new "Connected Flight Mode" technology, promising an evolution in airplane mode functionality. Unlike the current manual mode, this smart airplane mode will autonomously determine which...

Why You Need a Faraday Sleeve: Top 5 Reasons
In today's tech landscape, protecting personal information and digital assets is paramount. Faraday sleeves, which block all forms of electromagnetic radiation, present a compelling solution. Here are the top reasons...
Why You Need a Faraday Sleeve: Top 5 Reasons
In today's tech landscape, protecting personal information and digital assets is paramount. Faraday sleeves, which block all forms of electromagnetic radiation, present a compelling solution. Here are the top reasons...

Travel with Peace of Mind: 7 Tips for Digital S...
In today's interconnected world, digital threats are as real as physical ones, especially when traveling. Here are seven tips to help you stay digitally secure while you explore the...
Travel with Peace of Mind: 7 Tips for Digital Security on the Go
In today's interconnected world, digital threats are as real as physical ones, especially when traveling. Here are seven tips to help you stay digitally secure while you explore the...

Elon Musk Plans to Block iPhones with Faraday C...
Discover why Elon Musk plans to block iPhones using Faraday cages due to privacy concerns over Apple's new AI, Apple Intelligence. Learn about the AI's features, Musk's criticism, and his...
Elon Musk Plans to Block iPhones with Faraday Cages Due to Apple's New AI
Discover why Elon Musk plans to block iPhones using Faraday cages due to privacy concerns over Apple's new AI, Apple Intelligence. Learn about the AI's features, Musk's criticism, and his...
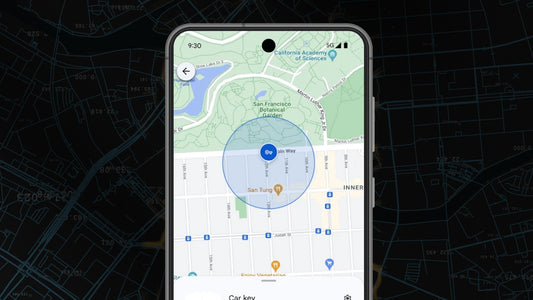
Google Transforms Every Android Phone into a Tr...
All Android smartphones will be connected to the "Find My Device" network, which tracks even powered-off phones. Explore how this system works, the potential privacy risks, and how to disable it.
Google Transforms Every Android Phone into a Tracker
All Android smartphones will be connected to the "Find My Device" network, which tracks even powered-off phones. Explore how this system works, the potential privacy risks, and how to disable it.

Is Your Smartphone Listening to You Right Now?
60% of people believe their mobile devices eavesdrop on conversations and deliver personalized ads accordingly. Mention something casually, and it seems to appear in advertisements almost instantly, as if your...
Is Your Smartphone Listening to You Right Now?
60% of people believe their mobile devices eavesdrop on conversations and deliver personalized ads accordingly. Mention something casually, and it seems to appear in advertisements almost instantly, as if your...
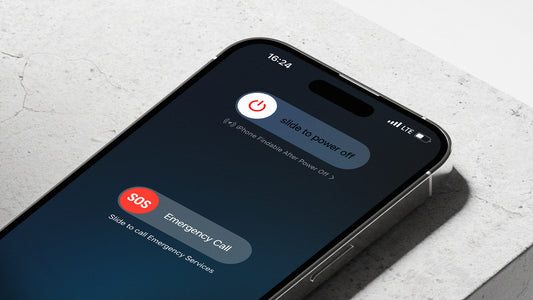
How Smartphones Continue Transmitting Data Even...
In the age of omnipresent connectivity, the notion of truly powering down seems like a relic of the past. Despite our best efforts to switch off our smartphones, modern devices...
How Smartphones Continue Transmitting Data Even When Turned Off
In the age of omnipresent connectivity, the notion of truly powering down seems like a relic of the past. Despite our best efforts to switch off our smartphones, modern devices...

iPhone Privacy Features: Falling Short of True ...
Explore the limitations of iPhone privacy features and uncover why they may not offer the security users expect in today's digital landscape.
iPhone Privacy Features: Falling Short of True Security
Explore the limitations of iPhone privacy features and uncover why they may not offer the security users expect in today's digital landscape.

5 Strategies to Safeguard Against Cyber Threats
In today's digital age, cyber threats and online scams are rampant. The less attention you pay to your digital security, the more vulnerable you become to sophisticated attackers. To help...
5 Strategies to Safeguard Against Cyber Threats
In today's digital age, cyber threats and online scams are rampant. The less attention you pay to your digital security, the more vulnerable you become to sophisticated attackers. To help...

NUIT Attacks: The Ultrasonic Trojan Redefining ...
NUIT Attacks: The Ultrasonic Trojan Redefining Digital Threats In a digital age where every electronic gadget is touted as 'smart,' a new threat stealthily emerges, threatening the perceived invulnerability of...
NUIT Attacks: The Ultrasonic Trojan Redefining Digital Threats
NUIT Attacks: The Ultrasonic Trojan Redefining Digital Threats In a digital age where every electronic gadget is touted as 'smart,' a new threat stealthily emerges, threatening the perceived invulnerability of...

Is It Safe to Sleep Beside a Mobile Phone? Expl...
Is It Safe to Sleep Beside a Mobile Phone? Exploring the Risks and Solutions The use of smartphones before bedtime has become a common practice. From setting alarms to scrolling...
Is It Safe to Sleep Beside a Mobile Phone? Exploring the Risks and Solutions
Is It Safe to Sleep Beside a Mobile Phone? Exploring the Risks and Solutions The use of smartphones before bedtime has become a common practice. From setting alarms to scrolling...

The Faraday Capsule: Safeguarding Corporate Sec...
7The Faraday Capsule: Safeguarding Corporate Secrets in the Digital Age In the glass-paneled offices of top executives, the chambers of high-ranking bureaucrats, and the meeting rooms of vast corporations, there...
The Faraday Capsule: Safeguarding Corporate Secrets in the Digital Age
7The Faraday Capsule: Safeguarding Corporate Secrets in the Digital Age In the glass-paneled offices of top executives, the chambers of high-ranking bureaucrats, and the meeting rooms of vast corporations, there...

Shielding Tester: A Pocket-Sized Faraday Cage T...
Shielding Tester: A Pocket-Sized Faraday Cage Tester for Android and iOS The Shielding Tester app is an essential utility for any shielding device user. With this app, you can independently...
Shielding Tester: A Pocket-Sized Faraday Cage Tester for Android and iOS
Shielding Tester: A Pocket-Sized Faraday Cage Tester for Android and iOS The Shielding Tester app is an essential utility for any shielding device user. With this app, you can independently...

Here's Why Your Gadgets Need a Faraday Cage
Here's Why Your Gadgets Need a Faraday Cage In our digital age, safe use of mobile devices is a significant challenge. This piece explores why control measures like a Faraday...
Here's Why Your Gadgets Need a Faraday Cage
Here's Why Your Gadgets Need a Faraday Cage In our digital age, safe use of mobile devices is a significant challenge. This piece explores why control measures like a Faraday...
Invasion of Digital Privacy: The Unseen Threat ...
Invasion of Digital Privacy: The Unseen Threat and How to Shield Yourself The Hidden Giant In the unexplored realms of the digital world lies a behemoth called WiGLE. Started in...
Invasion of Digital Privacy: The Unseen Threat and How to Shield Yourself
Invasion of Digital Privacy: The Unseen Threat and How to Shield Yourself The Hidden Giant In the unexplored realms of the digital world lies a behemoth called WiGLE. Started in...

French Senate Approves Law to Remotely Activate...
French Senate Approves Law to Remotely Activate Smartphone Cameras and Microphones The French Senate has given the green light to a law permitting security forces to remotely activate the camera...
French Senate Approves Law to Remotely Activate Smartphone Cameras and Microphones
French Senate Approves Law to Remotely Activate Smartphone Cameras and Microphones The French Senate has given the green light to a law permitting security forces to remotely activate the camera...

Understanding the Impact of Mobile Phone Radiat...
Understanding the Impact of Mobile Phone Radiation: A Comprehensive Guide What is Mobile Phone Radiation? Mobile phones, like many other electronic devices, emit non-ionizing radiation. This form of radiation, while...
Understanding the Impact of Mobile Phone Radiation: A Comprehensive Guide
Understanding the Impact of Mobile Phone Radiation: A Comprehensive Guide What is Mobile Phone Radiation? Mobile phones, like many other electronic devices, emit non-ionizing radiation. This form of radiation, while...

Velter’s Jammer Efficacy: Independent Laborator...
Velter’s Jammer Efficacy: Independent Laboratory Test Results As our digital era advances, conversations' privacy continues to dwindle. One of the threats we are facing is the non-consensual recording of private...
Velter’s Jammer Efficacy: Independent Laboratory Test Results
Velter’s Jammer Efficacy: Independent Laboratory Test Results As our digital era advances, conversations' privacy continues to dwindle. One of the threats we are facing is the non-consensual recording of private...

How to Block Your Phone and Go Off the Grid
How to Block Your Phone and Go Off the Grid In the current high-tech era, smartphones have emerged as essential tools for communication, navigation, and entertainment. We typically believe that,...
How to Block Your Phone and Go Off the Grid
How to Block Your Phone and Go Off the Grid In the current high-tech era, smartphones have emerged as essential tools for communication, navigation, and entertainment. We typically believe that,...

Protecting Yourself from Cyber Fraudsters: Esse...
Protecting Yourself from Cyber Fraudsters: Essential Tips for Digital Safety The modern digital world has witnessed a surge in technological advancements, but it has also given rise to cyber fraud...
Protecting Yourself from Cyber Fraudsters: Essential Tips for Digital Safety
Protecting Yourself from Cyber Fraudsters: Essential Tips for Digital Safety The modern digital world has witnessed a surge in technological advancements, but it has also given rise to cyber fraud...

The Trust Gap: Tech Titans Question WhatsApp's ...
The Trust Gap: Tech Titans Question WhatsApp's Privacy Elon Musk, CEO of Tesla and SpaceX, and Pavel Durov, founder of Telegram, have recently expressed their concerns over the privacy standards...
The Trust Gap: Tech Titans Question WhatsApp's Privacy
The Trust Gap: Tech Titans Question WhatsApp's Privacy Elon Musk, CEO of Tesla and SpaceX, and Pavel Durov, founder of Telegram, have recently expressed their concerns over the privacy standards...

Faraday Cases: The New Age Solution for Privacy...
Faraday Cases: The New Age Solution for Privacy and EMF Protection In today's digital age, where smartphones have become an indispensable part of our lives, there is growing concern about...
Faraday Cases: The New Age Solution for Privacy and EMF Protection
Faraday Cases: The New Age Solution for Privacy and EMF Protection In today's digital age, where smartphones have become an indispensable part of our lives, there is growing concern about...
What is SAR and How to Protect Yourself from Ph...
What is SAR and How to Protect Yourself from Phone Radiation The widespread use of smartphones has raised concerns about the potential health risks associated with electromagnetic radiation emitted by...
What is SAR and How to Protect Yourself from Phone Radiation
What is SAR and How to Protect Yourself from Phone Radiation The widespread use of smartphones has raised concerns about the potential health risks associated with electromagnetic radiation emitted by...

Keyless Car Theft: 7 Smart Ways to Protect Your...
Keyless Car Theft: 7 Smart Ways to Protect Your Vehicle Keyless car theft is on the rise, with criminals exploiting technology to gain access to vehicles without the need for...
Keyless Car Theft: 7 Smart Ways to Protect Your Vehicle
Keyless Car Theft: 7 Smart Ways to Protect Your Vehicle Keyless car theft is on the rise, with criminals exploiting technology to gain access to vehicles without the need for...

Is Your Phone Eavesdropping and Offering Ads?
Is Your Phone Eavesdropping and Offering Ads? Once is a coincidence, twice is a chance, and three times is a pattern. This formula accurately describes the situation with "eavesdropping" smartphones....
Is Your Phone Eavesdropping and Offering Ads?
Is Your Phone Eavesdropping and Offering Ads? Once is a coincidence, twice is a chance, and three times is a pattern. This formula accurately describes the situation with "eavesdropping" smartphones....
Your Phone is Tracking and Eavesdropping on You...
Your Phone is Tracking and Eavesdropping on You: An Expert Opinion In today's modern world, smartphones have become an essential part of our daily lives. They are not only a...
Your Phone is Tracking and Eavesdropping on You: An Expert Opinion
Your Phone is Tracking and Eavesdropping on You: An Expert Opinion In today's modern world, smartphones have become an essential part of our daily lives. They are not only a...

